This guide offers detailed instructions for configuring Symmetric IRB EVPN in SONiC, including VLAN setup, IP address configuration, L3VNI, VRF settings, VxLAN creation, and BGP environment establishment.
In our previous article, “Asymmetric IRB EVPN Testing Between SONiC and Cisco,” we provided detailed instructions for configuring interoperability testing of a Spine-Leaf topology using Asymmetric Integrated Routing and Bridging (IRB) Ethernet VPN (EVPN) between SONiC and Cisco.
Symmetric IRB
In symmetric IRB routing, both ingress and egress VTEPs perform IRB routing and bridging. The ingress VTEP routes packets to an egress VTEP MAC address in an intermediate virtual-network VNI. In this approach, all routed VXLAN traffic is directed through a dedicated transit VNI known as the L3VNI. This allows bidirectional traffic to traverse on the same VNI in both directions.
Using the L3 VNI associated with each tenant VRF, an ingress VTEP routes all traffic for the prefix to an egress VTEP on the L3 VNI. The egress VTEP routes from the L3 VNI to the destination virtual network or bridge domain. The L3 VNI does not have to be associated with an IP address; routing is set up in the data plane using the egress VTEP’s MAC address. This behavior is known as IP-VRF to IP-VRF interface-less routing. The ingress VTEP does not have to be configured with every destination virtual network; it must have the ARP and MAC addresses only to the egress VTEP, not to each host connected to the VTEP. For this reason, symmetric IRB routing allows the overlay network to scale larger than Asymmetric Routing.
Testbed & Image Version
- GNS3
- SONiC ( 202305 )
Topology
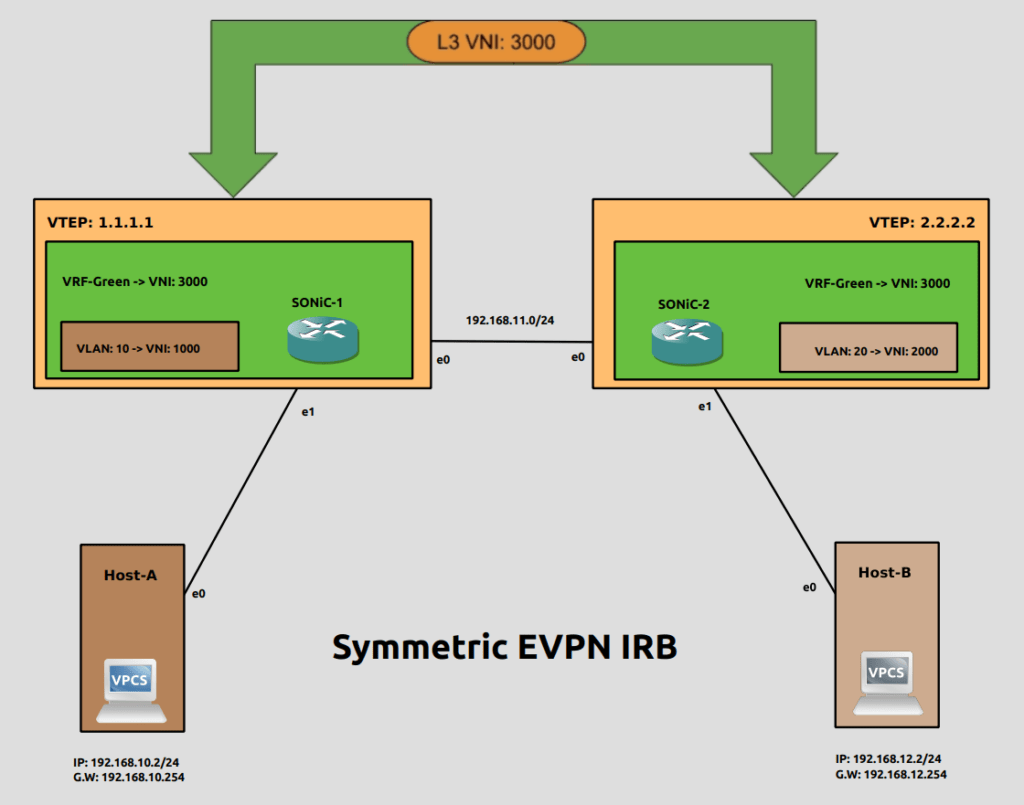
Steps to configure Symmetric IRB EVPN
- Setup VLAN Environment
- Configure IP addresses
- Configure VRF Setting
- Create VxLAN
- Configure layer3 VNI on a Switch
- Establish BGP environment for EVPN
Configurations on SONiC-1:
Step 1. Setup VLAN environment as per topology.
admin@sonic:~$ sudo config vlan add 10 admin@sonic:~$ sudo config vlan add 30 admin@sonic:~$ sudo config vlan member add -u 10 Ethernet4
Step 2. Configure IP addresses.
admin@sonic:~$ sudo config interface ip add Ethernet0 192.168.11.1/24 admin@sonic:~$ sudo config interface ip add Loopback10 1.1.1.1/32
Step 3. Configure VRF Setting.
admin@sonic:~$ sudo config vrf add Vrf-Green admin@sonic:~$ sudo config interface vrf bind Vlan30 Vrf-Green admin@sonic:~$ sudo config interface vrf bind Vlan10 Vrf-Green admin@sonic:~$ sudo config interface ip add Vlan10 192.168.10.254/24
Below is the status of the VLAN table.
admin@sonic:~$ show vlan brief +-----------+-------------------+-----------+----------------+-------------+-----------------------+ | VLAN ID | IP Address | Ports | Port Tagging | Proxy ARP | DHCP Helper Address | +===========+===================+===========+================+=============+=======================+ | 10 | 192.168.10.254/24 | Ethernet4 | untagged | disabled | | +-----------+-------------------+-----------+----------------+-------------+-----------------------+ | 30 | | | | disabled | | +-----------+-------------------+-----------+----------------+-------------+-----------------------+
Step 4. Create VxLAN.
admin@sonic:~$ sudo config vxlan add vtep 1.1.1.1 admin@sonic:~$ sudo config vxlan evpn_nvo add nvo vtep admin@sonic:~$ sudo config vxlan map add vtep 10 1000 admin@sonic:~$ sudo config vxlan map add vtep 30 3000 admin@sonic:~$ sudo config save -y
The figure below depicts that VxLAN tunnel is successfully created.
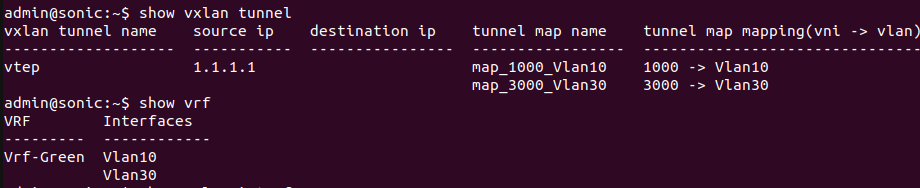
Step 5. Set the layer3 VNI on a switch.
admin@sonic:~$ sudo config vrf add_vrf_vni_map Vrf-Green 3000
Step 6. Establish a BGP environment for EVPN.
admin@sonic:~$ vtysh Hello, this is FRRouting (version 8.5.1). Copyright 1996-2005 Kunihiro Ishiguro, et al. sonic# configure sonic(config)# no router bgp 65100 sonic(config)# router bgp 65000 sonic(config-router)# neighbor 192.168.11.2 remote-as 65000 sonic(config-router)# address-family ipv4 unicast sonic(config-router-af)# network 1.1.1.1/32 sonic(config-router-af)# exit sonic(config-router)# address-family l2vpn evpn sonic(config-router-af)# neighbor 192.168.11.2 activate sonic(config-router-af)# advertise-all-vni sonic(config-router-af)# end sonic# configure terminal sonic(config)# vrf Vrf-Green sonic(config-vrf)# vni 3000 sonic(config-vrf)# end sonic# configure terminal sonic(config)# router bgp 65000 vrf Vrf-Green sonic(config-router)# address-family ipv4 unicast sonic(config-router-af)# redistribute connected sonic(config-router-af)# exit sonic(config-router)# address-family l2vpn evpn sonic(config-router-af)# advertise ipv4 unicast sonic(config-router-af)# end sonic# wr Note: this version of vtysh never writes vtysh.conf Building Configuration... Configuration saved to /etc/frr/zebra.conf Configuration saved to /etc/frr/bgpd.conf Configuration saved to /etc/frr/staticd.conf
Configurations on SONiC-2:
Step 1. Setup VLAN environment as per topology.
admin@sonic:~$ sudo config vlan add 20 admin@sonic:~$ sudo config vlan add 30 admin@sonic:~$ sudo config vlan member add -u 20 Ethernet4
Step 2. Configure IP addresses.
admin@sonic:~$ sudo config interface ip add Ethernet0 192.168.11.2/24 admin@sonic:~$ sudo config interface ip add Loopback10 2.2.2.2/32
Step 3. Configure VRF Setting.
admin@sonic:~$ sudo config vrf add Vrf-Green admin@sonic:~$ sudo config interface vrf bind Vlan30 Vrf-Green admin@sonic:~$ sudo config interface vrf bind Vlan20 Vrf-Green admin@sonic:~$ sudo config interface ip add Vlan20 192.168.12.254/24
Below is the status of the VLAN table.
admin@sonic:~$ show vlan brief +-----------+-------------------+-----------+----------------+-------------+-----------------------+ | VLAN ID | IP Address | Ports | Port Tagging | Proxy ARP | DHCP Helper Address | +===========+===================+===========+================+=============+=======================+ | 20 | 192.168.12.254/24 | Ethernet4 | untagged | disabled | | +-----------+-------------------+-----------+----------------+-------------+-----------------------+ | 30 | | | | disabled | | +-----------+-------------------+-----------+----------------+-------------+-----------------------+
Step 4. Create VxLAN.
admin@sonic:~$ sudo config vxlan add vtep 2.2.2.2 admin@sonic:~$ sudo config vxlan evpn_nvo add nvo vtep admin@sonic:~$ sudo config vxlan map add vtep 20 2000 admin@sonic:~$ sudo config vxlan map add vtep 30 3000 admin@sonic:~$ sudo config save -y
The figure below depicts that VxLAN tunnel is successfully created.
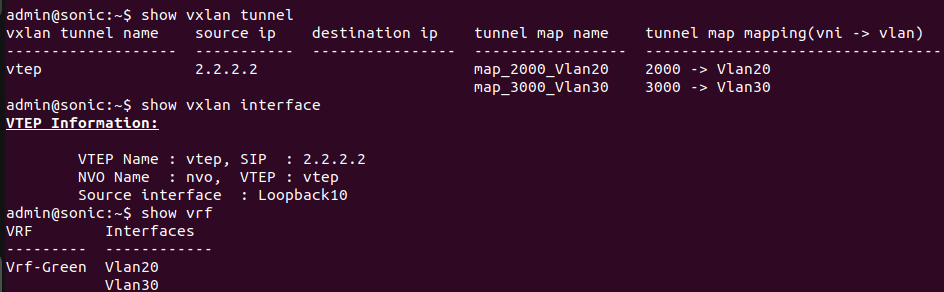
Step 5. Set the layer3 VNI on a switch.
admin@sonic:~$ sudo config vrf add_vrf_vni_map Vrf-Green 3000
Step 6. Establish a BGP environment for EVPN.
admin@sonic:~$ vtysh Hello, this is FRRouting (version 8.5.1). Copyright 1996-2005 Kunihiro Ishiguro, et al. sonic# configure sonic(config)# no router bgp 65100 sonic(config)# router bgp 65000 sonic(config-router)# neighbor 192.168.11.1 remote-as 65000 sonic(config-router)# address-family ipv4 unicast sonic(config-router-af)# network 2.2.2.2/32 sonic(config-router-af)# exit sonic(config-router)# address-family l2vpn evpn sonic(config-router-af)# neighbor 192.168.11.1 activate sonic(config-router-af)# advertise-all-vni sonic(config-router-af)# end sonic# configure terminal sonic(config)# vrf Vrf-Green sonic(config-vrf)# vni 3000 sonic(config-vrf)# end sonic# configure terminal sonic(config)# router bgp 65000 vrf Vrf-Green sonic(config-router)# address-family ipv4 unicast sonic(config-router-af)# redistribute connected sonic(config-router-af)# exit sonic(config-router)# address-family l2vpn evpn sonic(config-router-af)# advertise ipv4 unicast sonic(config-router-af)# end sonic# wr Note: this version of vtysh never writes vtysh.conf Building Configuration... Configuration saved to /etc/frr/zebra.conf Configuration saved to /etc/frr/bgpd.conf Configuration saved to /etc/frr/staticd.conf
Results of SONiC-1
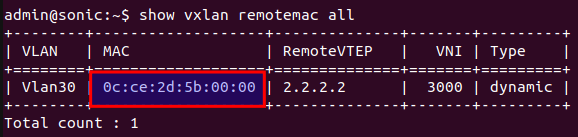
The figure below shows that the remote VTEP (DIP) is learned through EVPN.
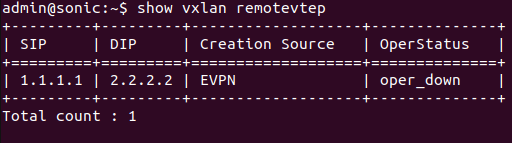
The result below shows that the MAC address of the destination VTEP is learned, which is the main functionality of Symmetric IRB EVPN using L3VNI.
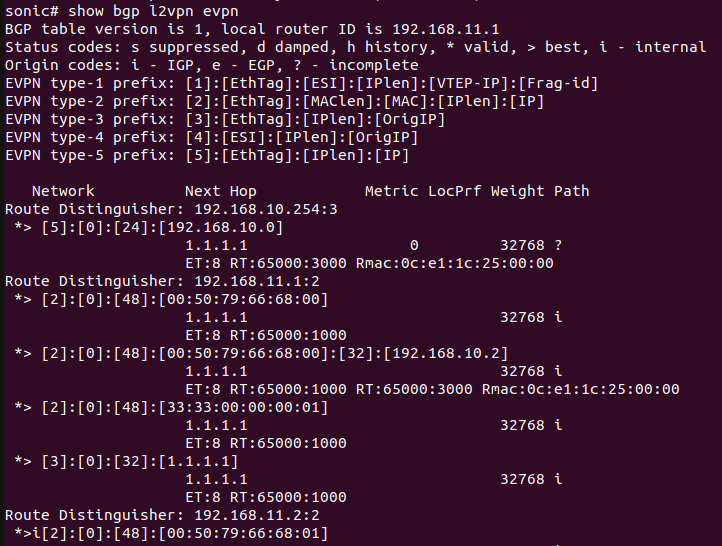
Below is the status of EVPN Route Types.
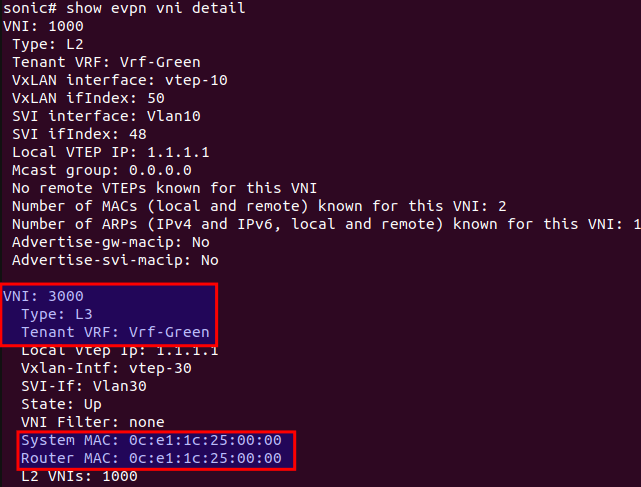
The figure below shows that it is a L3 VxLAN with Symmetric IRB because an L3 VNI is used in this topology.
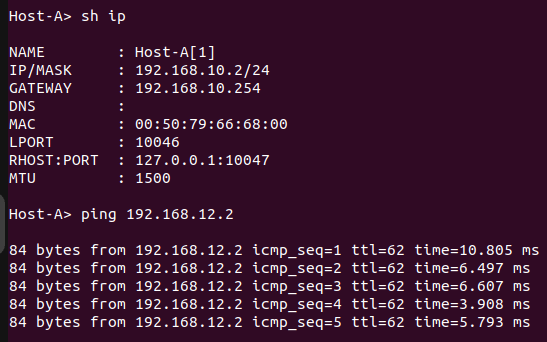
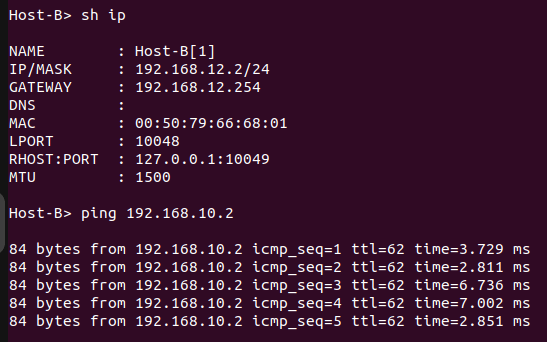
When the ping request is generated from Host A, it successfully receives a reply from Host B and vice versa.
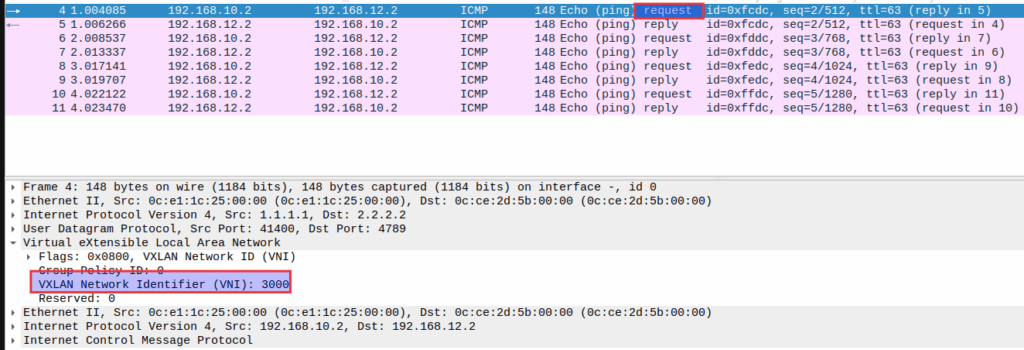
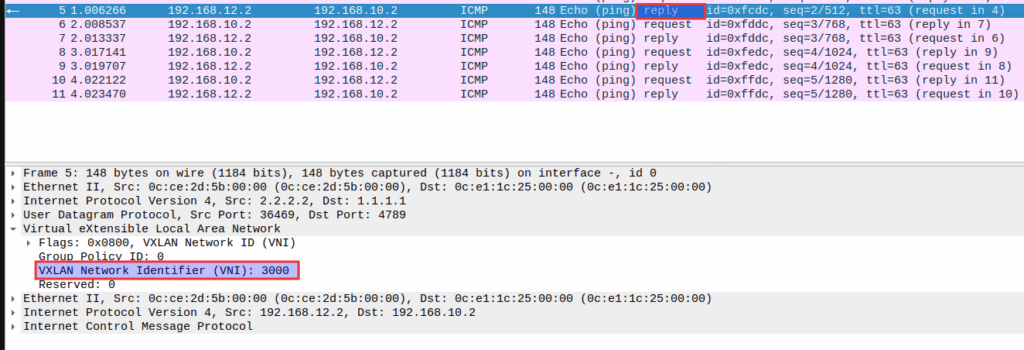
For better understanding, packets are captured with Wireshark. The figure below shows that when Host A sends the traffic to Host B then VTEP1 tunnels the traffic in the L3VNI 3000 to VTEP2 and vice versa.
References
About Hardware Nation:
Hardware Nation is a professional services company that accelerates network transformation through an open networking approach, enabling freedom of choice, flexibility, and cost efficiency. Our seasoned experts have worked on projects for some of the world’s leading organizations, leveraging a hybrid cloud-first and AI-enabled approach. We help our customers navigate the ecosystem, drawing on decades of experience. Our deployments are powered by leading white box and OEM network, compute, and storage vendors. Our expertise encompasses a wide range of industries and use cases, including enterprise, cloud, data center, AI, 5G/ISP infrastructure, and edge IT.
Humza Atlaf
Network Engineer
Humza is a network engineer at Hardware Nation Labs, where his passion for Open Networking drives his work. With a blend of deep expertise and innovative approaches, he designs robust, scalable networks of the future. His practical experience includes configuring and deploying a range of protocols such as LACP, VLANs, MPLS, and VRRP. At his previous role, he was part of a SONiC testing team, further honing his skills in network setup and troubleshooting. Humza is also adept at network analysis with tools like Wireshark, enhancing his ability to manage complex network environments.
Alex Cronin
Co-Founder and Solutions Architect
Alex Cronin is a seasoned Solutions Architect with over 15 years of experience in networking and disaggregated infrastructure. His career is defined by aligning enterprise technology with business needs across diverse market segments, from emerging startups to Fortune 500 companies. He has worked on digital infrastructure projects covering network design and software solutions for data center operators, service providers, and enterprises. He is continuously collaborating with Hardware Nation Labs R&D to explore and pioneer the latest advancements in open networking and is assessing the applicability of AI/ML technology across enterprise, data center, and service provider infrastructures.




